Cyber menace looking is a proactive safety measure taken to detect and neutralize potential threats on a community earlier than they trigger vital injury. To search out this kind of menace, safety professionals use cyber threat-hunting instruments. These are software program options pushed by superior analytics, machine studying, and synthetic intelligence to detect irregular patterns in a system’s community and endpoints. They use methods like behavioral analytics, sample matching, statistical evaluation, and AI/ML modeling.
With reports from Statista indicating that 72% of companies worldwide have been affected by ransomware assaults in 2023, extra organizations are searching for cyber menace looking options this yr.
In this information, we discover the highest cyber threat-hunting instruments for 2024 and examine their options, advantages, and downsides.
ESET PROTECT Advanced
Employees per Company Size
Micro (0-49), Small (50-249), Medium (250-999), Large (1,000-4,999), Enterprise (5,000+)
Any Company Size
Any Company Size
Features
Advanced Threat Defense, Full Disk Encryption , Modern Endpoint Protection, and extra
HandleEngine Log360
Employees per Company Size
Micro (0-49), Small (50-249), Medium (250-999), Large (1,000-4,999), Enterprise (5,000+)
Micro (0-49 Employees), Small (50-249 Employees), Medium (250-999 Employees), Large (1,000-4,999 Employees), Enterprise (5,000+ Employees)
Micro, Small, Medium, Large, Enterprise
Features
Activity Monitoring, Blacklisting, Dashboard, and extra
Graylog
Employees per Company Size
Micro (0-49), Small (50-249), Medium (250-999), Large (1,000-4,999), Enterprise (5,000+)
Medium (250-999 Employees), Large (1,000-4,999 Employees), Enterprise (5,000+ Employees)
Medium, Large, Enterprise
Features
Activity Monitoring, Dashboard, Notifications
Top menace looking options comparability
The desk under lists high menace looking options and the way their options examine.
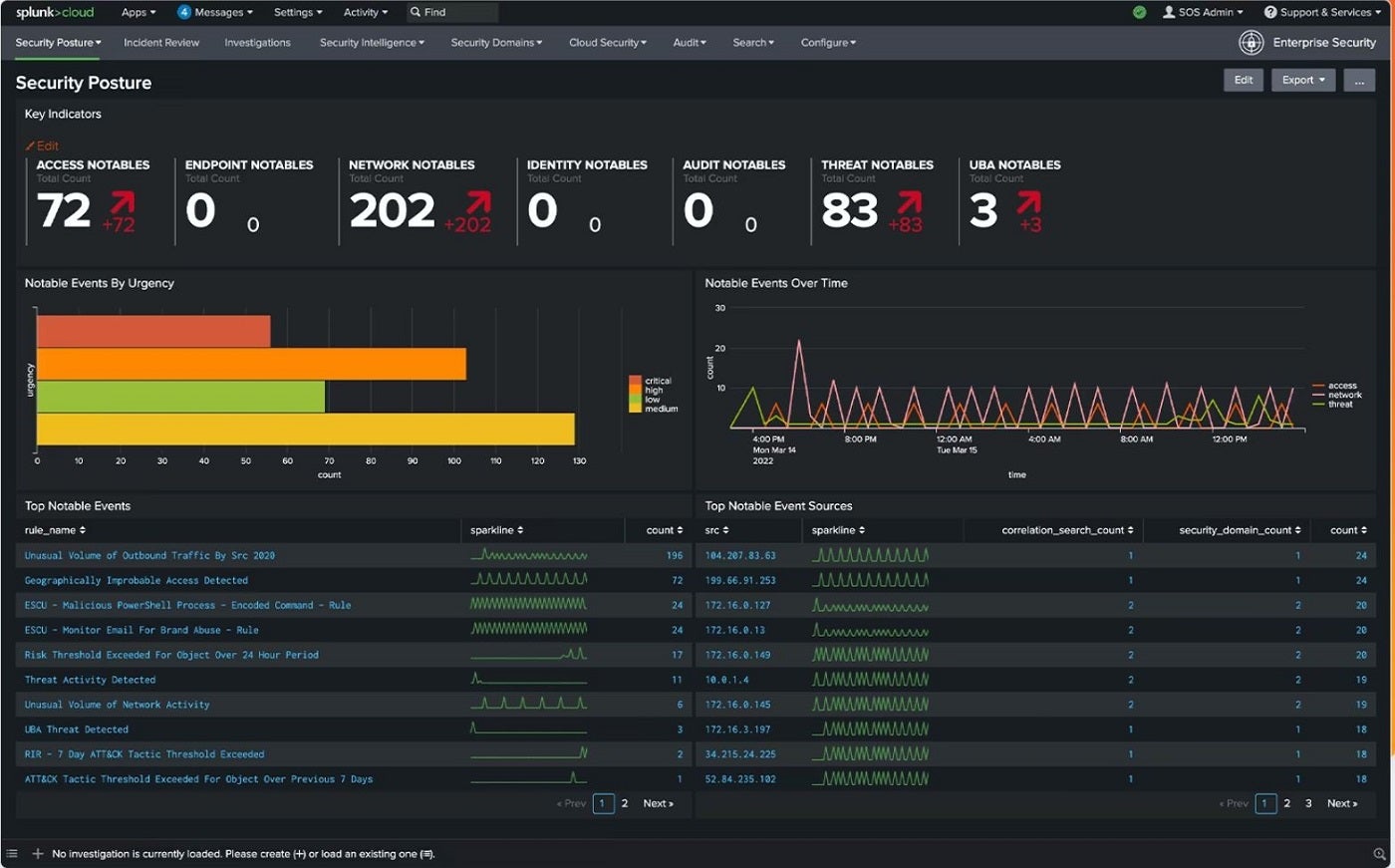
For the perfect total cyber menace looking device, I like to recommend Splunk. Offering cloud, on-premises, and hybrid options, Splunk as a safety info and occasion administration system is top-tier answer to proactively deal with hidden threats. It brings sturdy information question performance that caters to bigger safety operation features, resembling large-scale menace looking in enterprises.
SEE: 5 Best Endpoint Detection & Response Solutions for 2024 (TechRepublic)
Through Splunk, safety groups can generate threat-hunting queries, evaluation routines, and automatic defensive guidelines. A spotlight of Splunk’s SIEM capabilities is its pace, having the ability to detect threats shortly for early stage detection and remediation. It additionally gives superior menace detection with about 1,400 detection frameworks and an open, extensible information monitoring platform.
Why I selected Splunk
I selected Splunk for its sturdy menace looking capabilities, offering quick detection and evaluation irrespective of the menace. I even have it on the highest spot for being well-suited to deal with looking achieved in giant enterprises and organizations. This is particularly seen by way of its range in cloud, on-premises, or hybrid menace looking and intensive detection framework.
Pricing
This answer presents a 14-day trial interval. For pricing, contact the seller.
Features
- Multi-platform integration.
- Open, extensible information monitoring platform.
- Incident evaluation dashboard for fast prioritization of threats.
- Security posture dashboard and menace topology.
- Advanced menace detection.
- Risk-based alerting.
Pros and cons
| Pros | Cons |
|---|---|
| Offers menace intelligence administration. | Pricing is ambiguous. |
| Publicly out there menace looking guides. | |
| Customizable occasion prioritization. | |
| Flexible deployment choices. | |
| Rapid and responsive safety content material updates. | |
| Scalable enterprise-focused menace detection and evaluation. |
VMware Carbon Black Endpoint: Best for offline and hybrid environments

If you’re employed in a hybrid or offline setting, I recommend VMware Carbon Black Endpoint, developed by VMware. It’s a threat-hunting device geared up with behavioral endpoint detection and response (EDR), prolonged detection and response (XDR), and a next-generation antivirus (NGAV). These options mix with its machine studying functionality to ship superior menace looking. The answer repeatedly data and analyzes endpoint exercise and behaviors to detect superior threats.
SEE: 4 Threat Hunting Techniques to Prevent Bad Actors in 2024 (TechRepublic)
I significantly like how Carbon Black Endpoint can leverage unsupervised machine studying fashions, having the ability to detect anomalies that will point out malicious exercise throughout the cyber kill chain. While its Standard model lacks audit and remediation, I’m assured organizations can achieve satisfactory EDR visibility in offline, hybrid, and disconnected environments.
Why I selected VMware Carbon Black Endpoint
I’ve VMware Carbon Black Endpoint on this record because of its EDR visibility that covers offline, air-gapped, and disconnected environments.
Pricing
Reach out to the seller for pricing.
Features
- Next-gen antivirus.
- Behavioral Endpoint Detection and Response (EDR).
- Anomaly detection.
- Increased endpoint and container visibility.
- Automated menace looking.
Pros and cons
| Pros | Cons |
|---|---|
| Integration with standard safety instruments like Splunk, LogRhythm, and Proofpoint. | No audit and remediation in the usual model. |
| Supports compliance and audit options. | |
| Endpoint visibility inside and out of doors of the company community. | |
| Advanced Predictive Cloud Security. | |
| Mutual menace change between shoppers. |
CrowdStrike Falcon Overwatch: Best for superior menace looking

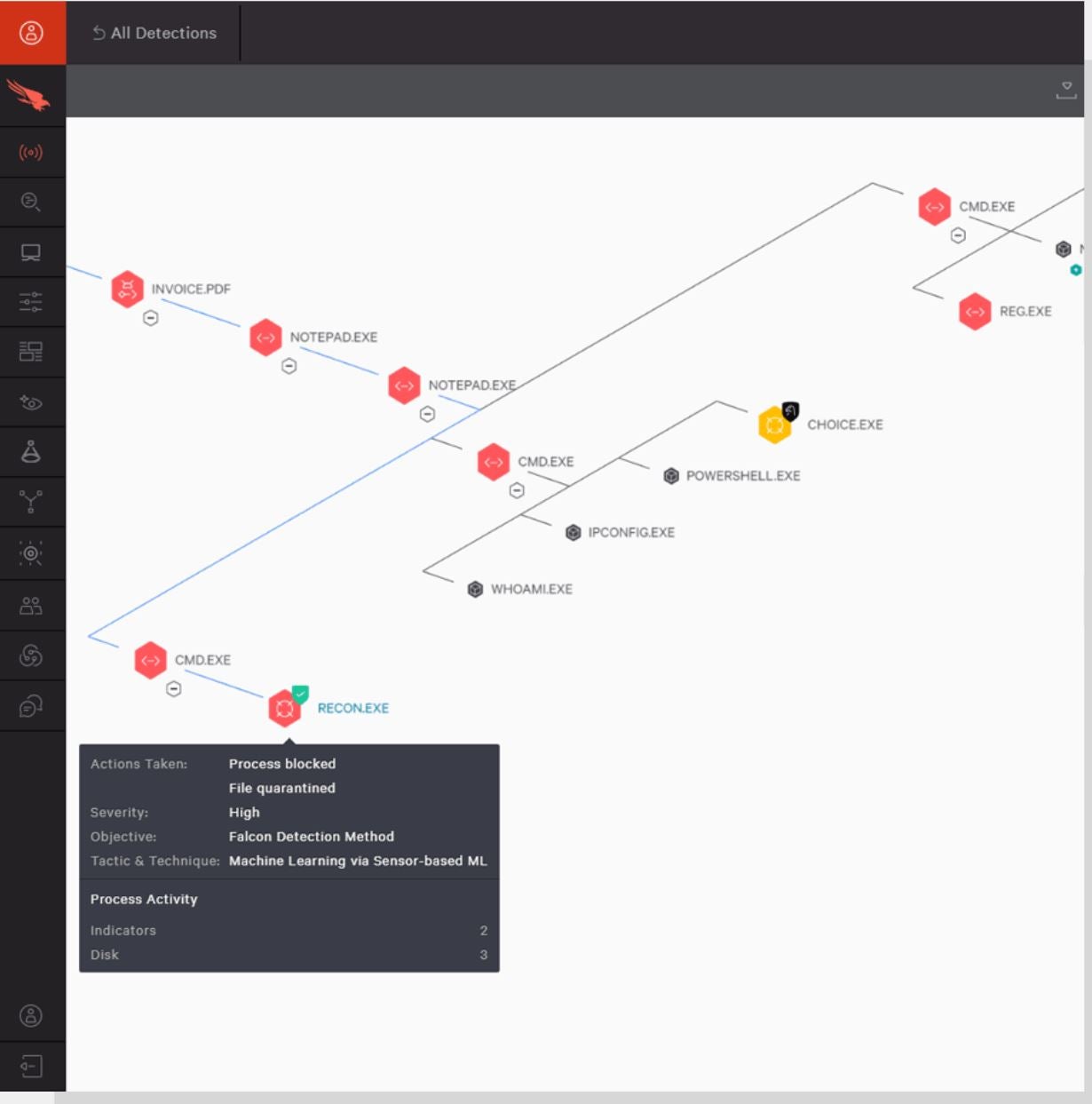
If you intend to conduct superior menace looking particularly, I recommend CrowdStrike Falcon Overwatch with superior EDR and XDR. CrowdStrike’s Overwatch makes use of its SEARCH methodology to hunt and cease threats. Through this system, CrowdStrike’s Overwatch leverages cloud-scale information, insights from in-house analysts, and menace intelligence to mine giant quantities of information for indicators of intrusion or assault. Also, its light-weight sensor watches and collects information from an unlimited vary of endpoint occasions uploaded to its cloud storage for evaluation.
SEE: CrowdStrike vs Trellix (2024): What Are the Main Differences? (TechRepublic)
An Overwatch characteristic I discover significantly spectacular is its menace graph, which helps cyber analysts decide the origins of threats and the way they might unfold. This can present helpful perception in adopting proactive safety measures to forestall any future assaults.
Why I selected CrowdStrike Falcon Overwatch
I picked CrowdStrike Falcon Overwatch for its devoted method to superior menace looking and automatic response to threats, which is achieved by a mix of superior EDR, XDR, and proprietary options.
Pricing
The CrowdStrike Falcon Overwatch presents a 15-day free trial and options two plans: the Falcon Overwatch and Falcon Overwatch Elite. Contact the seller for a quote.
SEE: CrowdStrike vs Sophos (2024): Which Solution Is Better for Your Business? (TechRepublic)
Features
- Advanced EDR and XDR.
- Visibility with Falcon USB Device management.
- Automated menace intelligence.
- Threat Graph.
- Firewall administration.
Pros and cons
| Pros | Cons |
|---|---|
| Threat alerts are augmented with context. | Threat looking and investigation teaching are unique to Falcon Overwatch Elite customers. |
| Includes choices for managed service. | |
| Offers a 15-day free trial. | |
| XDR capabilities for superior menace detection and response. | |
| Quarterly menace looking studies. |
SolarWinds Security Event Manager: Best for centralized menace administration

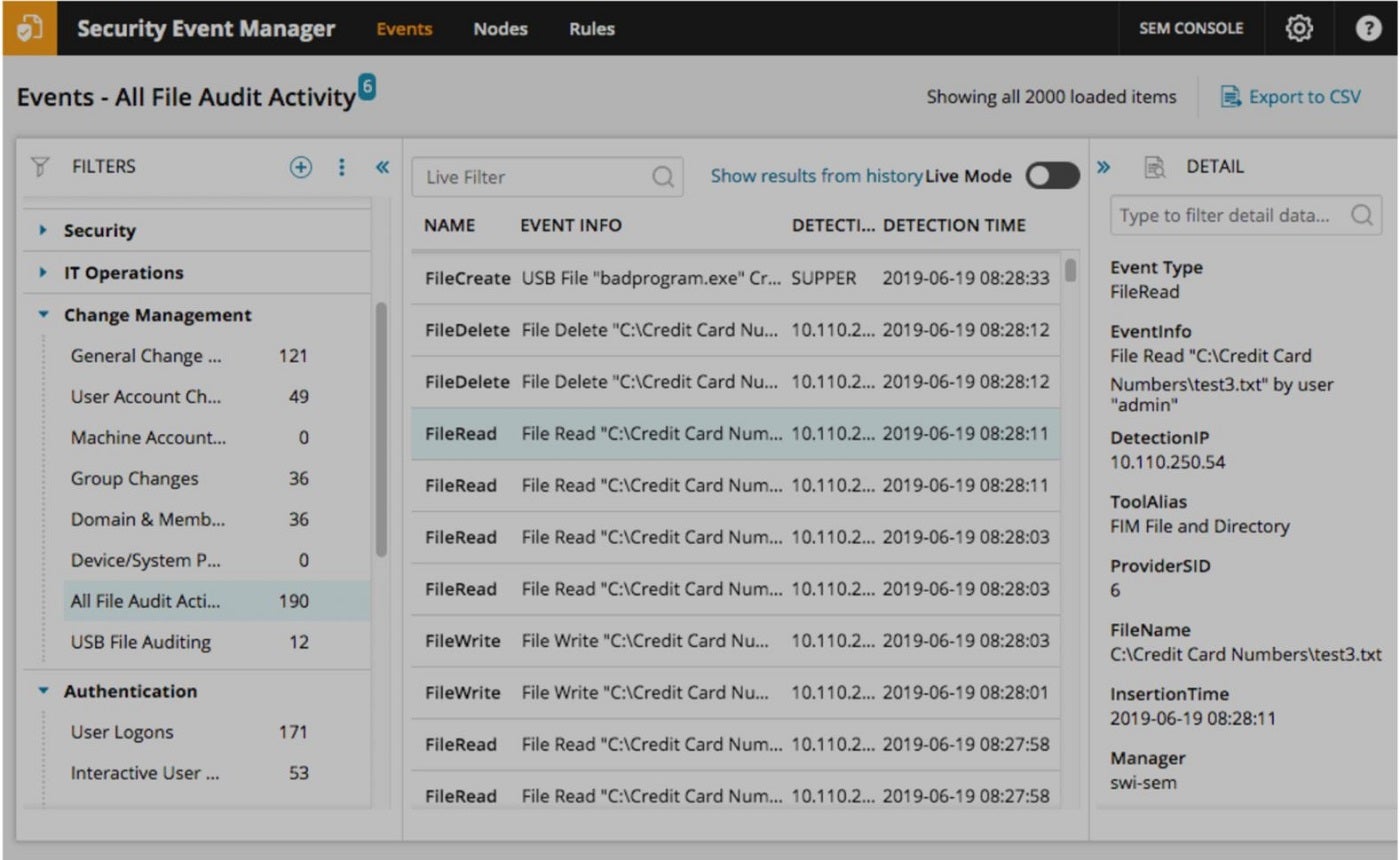
For customers centralized menace administration, I discover SolarWinds Security Event Manager delivers properly. SolarWinds gives its menace looking capabilities by way of a mix of real-time community efficiency statistics and information derived from numerous sources, such because the Simple Network Management Protocol (SNMP) and log entries. The info derived from SNMP permits the system to assemble information about community units, efficiency metrics, and different important points in real-time.
SEE: Top 8 Advanced Threat Protection Tools and Software for 2024 (TechRepublic)
By parsing and deciphering log information, SEM can establish patterns, anomalies, and potential threats. For me, SEM’s central hub is a noteworthy characteristic inclusion. It allows safety groups to assemble, analyze, and reply to safety occasions produced by various safety applied sciences, resembling firewalls, intrusion detection techniques, and endpoint safety options.
Why I selected SolarWinds Security Event Manager
I selected SEM because of its centralized platform and seamless integration with numerous safety applied sciences, providing streamlined safety administration. This helps safety professionals get a chook’s eye view of all potential threats or information that would result in discovering vulnerabilities or potential weaknesses.
Pricing
SolarWinds Event Manager presents subscription and perpetual licensing plans. Contact the seller for a customized quote.
Features
- Built-in file integrity monitoring.
- Centralized log assortment and normalization.
- Integrated compliance reporting instruments.
- Advanced pfSense firewall log analyzer.
- Advanced persistent menace (APT) safety software program.
Pros and cons
| Pros | Cons |
|---|---|
| Offers real-time community efficiency statistics. | Absence of cloud model. |
| Centralized logon audit occasions monitor for monitoring of safety occasions. | |
| Improved safety, real-time monitoring and troubleshooting with superior pfSense firewall log analyzer. | |
| Integrates with numerous safety applied sciences for higher visibility. | |
| Provides in-depth evaluation of log entries to boost menace detection. |
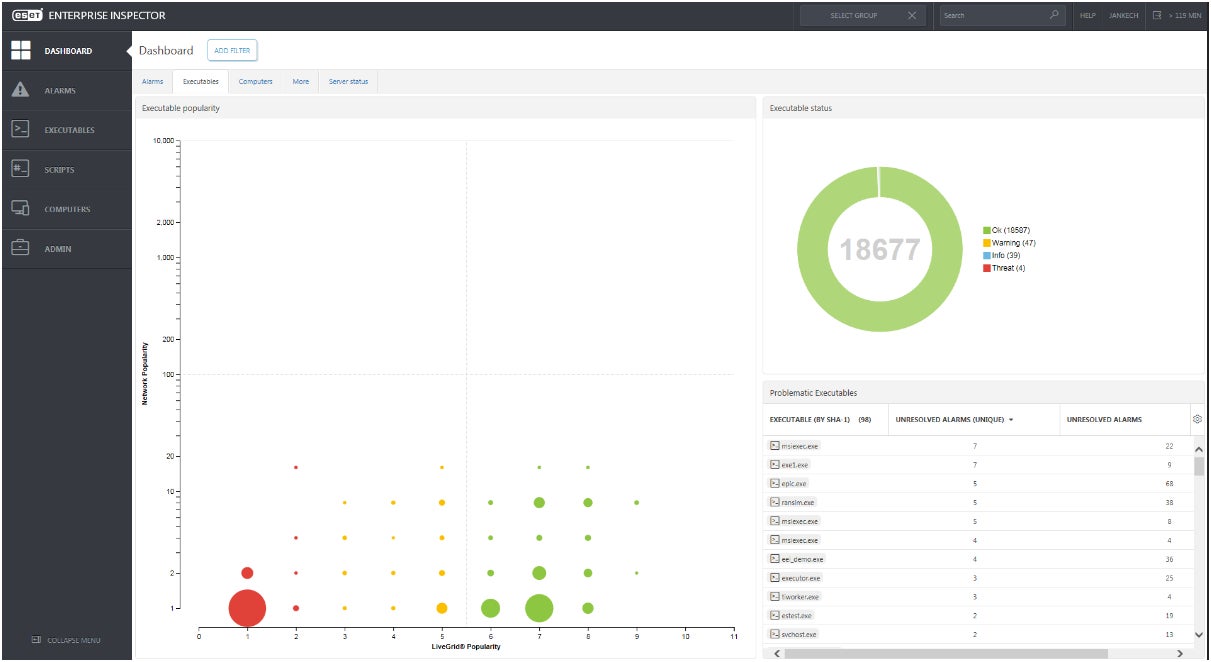
ESET Enterprise Inspector: Best for tandem menace looking service

If your organization is searching for menace looking companies alongside a devoted software program device, I recommend ESET Enterprise Inspector. Enterprise Inspector is ESET’s EDR device that’s constructed to research actual time endpoint information and detect persistent threats. Its EDR has the flexibility to re-scan total occasions databases, making it supreme for historic menace looking. This additionally helps menace hunters simply discover new indicators of compromise by adjusting detection guidelines as they scan the database.
I particularly like how ESET gives their very own ESET Threat Hunting service, in tandem with ESET Enterprise Inspector. This is good for organizations that don’t have the manpower or devoted safety workers to endure cyber menace looking.
Why I selected ESET Inspector
I’ve ESET Inspector on this record as a result of it presents a devoted menace looking service alongside its ESET Enterprise Inspector EDR. I really feel this can be a nice answer for smaller companies that don’t have intensive IT or safety groups however nonetheless need to reap the advantages of superior cyber menace looking.
Pricing
It’s greatest to contact ESET’s Sales group for curated pricing and a correct citation.
Features
- Behavior and reputation-based detection.
- Automated menace looking capabilities.
- Can be accompanied with devoted menace looking service.
- Protection towards file much less assaults.
- Customizable alerts.
Pros and cons
| Pros | Cons |
|---|---|
| Easily adjustable detection guidelines. | May be resource-intensive for older techniques. |
| In cloud or on-premises deployment. | |
| Good for companies with minimal safety experience. | |
| Integrates with different ESET options for synchronized response. | |
| Seamless deployment. |
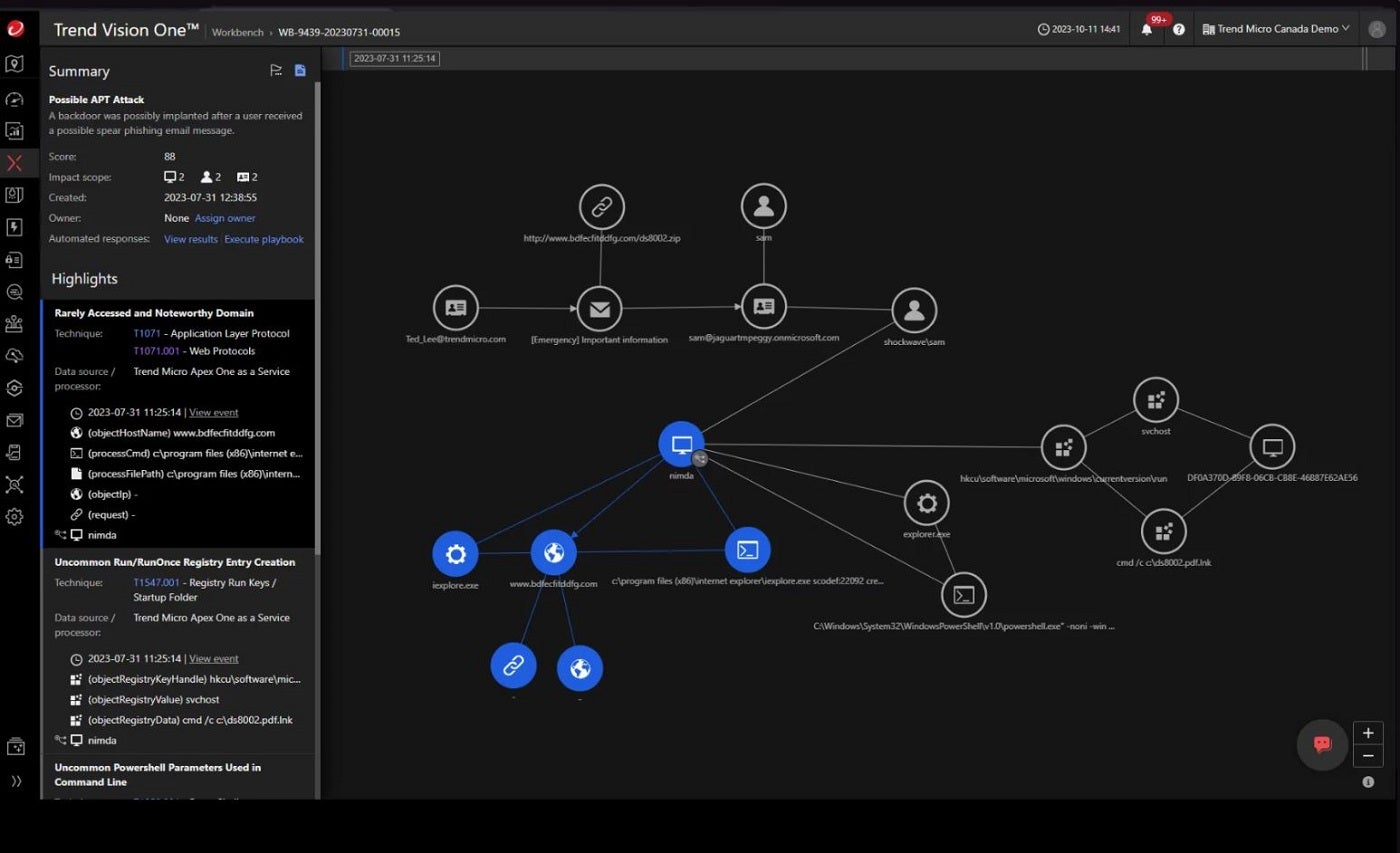
Trend Micro Managed XDR: Best for devoted SOC help

If you want a service with devoted SOC help, I encourage you to take a look at Trend Micro Managed XDR. Its safety service presents 24/7 monitoring and evaluation and stands out for its potential to correlate information from a variety of sources, together with e-mail, endpoint, server, cloud, workload, and community.
I commend Trend Micro for this cross-layered method, because it enhances menace looking and gives larger perception into the supply and unfold of focused assaults. The answer repeatedly scans for indicators of compromise or assault, together with these shared through US-CERT and third-party disclosures, guaranteeing a proactive method to menace looking.
Another standout to me is how Managed XDR gives devoted help for Security Operations Center (SOC) groups, lowering the time to establish, examine, and reply to threats. As a part of Trend Service One, it consists of premium help and incident response companies, extending its worth throughout the product.
Why I selected Trend Micro Managed XDR
I picked Trend Micro Managed XDR for its 24/7 help for Security Operations Center (SOC) groups, and its threat-hunting capabilities that improve time-to-detect and time-to-respond efficiency.
Pricing
Trend Micro Managed XDR presents a 30-day free trial. Contact the seller for pricing.
Features
- Endpoint detection and response.
- 24/7 evaluation and monitoring.
- Advanced menace intelligence.
- Cross-layered detection and response.
- Optimized safety analytics.
Pros and cons
| Pros | Cons |
|---|---|
| Dedicated help for SOC and IT safety groups. | Lack of on-premises answer. |
| Offers server and e-mail safety. | |
| Proactive menace attempting to find superior threats. | |
| Contains threats and robotically generates IoCs to forestall future assaults. | |
| Generates menace alerts and detailed incident studies. |
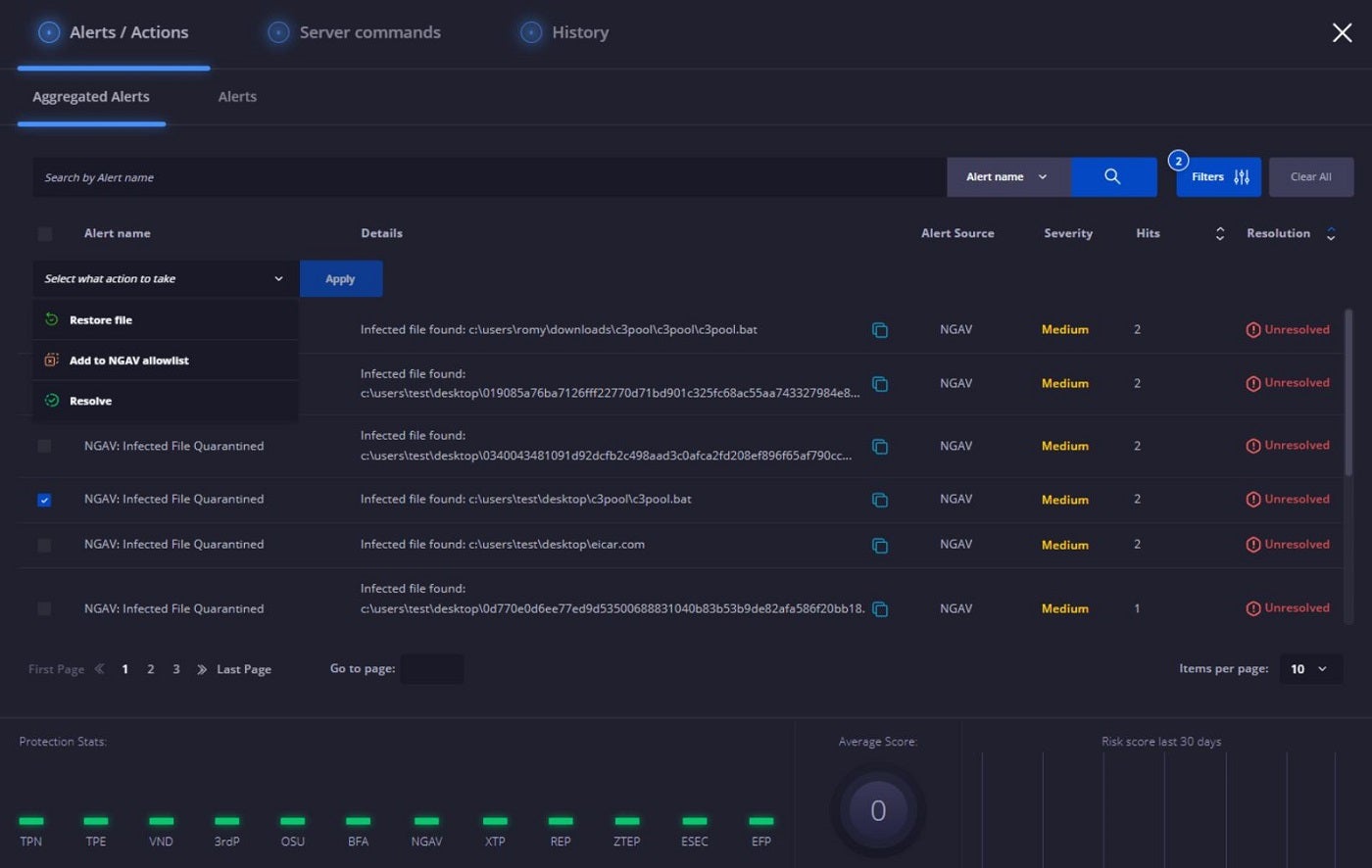
Heimdal Threat Hunting and Action Center: Best for single-command menace mitigation

For handy, single-command mitigation, I like Heimdal Threat Hunting and Action Center. Heimdal’s menace looking and detection answer equips SecOps groups and IT directors with instruments for figuring out and monitoring anomalous conduct throughout units and networks. Leveraging its superior XTP engine, the Heimdall suite, and the MITRE ATT&CK framework, this platform visualizes related info associated to endpoints for network-level menace detection.
Users achieve insights by way of danger scores and forensic evaluation, which boosts their understanding of potential threats. I personally recognize the continual scanning by the XTP engine — including a strategic layer to menace identification and monitoring. It additionally permits for immediate remediation with a single command wherever threats are recognized.
Why I selected Heimdal Threat Hunting and Action Center
To me, Heimdal stands out due to its one-click execution of instructions like scanning, quarantine, and isolation, together with in-depth incident investigation powered by its Action Center.
Pricing
Contact the seller for a quote.
Features
- Next-gen antivirus, firewall, and cell machine administration (MDM).
- Incident investigation and administration.
- Activity monitoring and monitoring.
- XTP Engine and MITRE ATT&CK framework.
- Quarantine performance.
Pros and cons
| Pros | Cons |
|---|---|
| Provides a centralized record of the threats detected. | No pricing info out there on-line. |
| Real-time menace monitoring and alerts are supplied. | |
| Makes for immediate reporting and statistics. | |
| Single-command remediation is feasible with the motion heart. | |
| Provides a unified view for intelligence, looking, and response. | |
Key Features of Cyber Threat Hunting Tools
From log evaluation and proactive menace identification to intelligence sharing, menace looking options may be geared up with a number of options that separate them from conventional safety monitoring instruments. Below are some key options I really feel each threat-hunting device ought to possess.
Data assortment and evaluation
Threat looking instruments collect and combination huge quantities of information from numerous sources, resembling logs, occasions, endpoint telemetry, and community visitors. Leveraging superior analytics and machine studying, uncommon patterns and anomalies are decided. These options improve their understanding of potential threats by reviewing or scrutinizing alerts from SIEM techniques and Intrusion detection techniques (IDS). They analyze the info gathered from firewalls, IDS, DNS, file and person information, antivirus options, and different safety units for higher perception on what to categorize as potential threats and greatest remediation channels.
Proactive search and identification of threats
This characteristic helps safety analysts discover and examine intensive information collected from numerous sources. The superior search and question language help allows them to go looking, filter, and question the info. To do that, safety groups can customise and streamline their searches based mostly on sure organizational necessities to extract info like time ranges, particular IP addresses, person accounts, or sorts of actions. One of crucial points of this characteristic is that not solely does it carry out real-time evaluation by querying reside information streams to establish ongoing threats promptly, however it additionally performs historic information evaluation that identifies previous incidents or patterns which may have gone unnoticed initially.
SEE: Why Your Business Needs Cybersecurity Awareness Training (TechRepublic Premium)
Collaboration and intelligence sharing
Threat looking goes past particular person initiatives, as the info collected and processed individually can be restricted. Effective collaboration and intelligence sharing amongst organizations, safety groups, and trade companions are important, and this could solely be achieved by integrating sharable menace intelligence feeds in menace looking instruments. The change of menace intelligence, techniques, methods, and procedures (TTPs) facilitates menace looking and remediation throughout various organizations.
Behavioral evaluation
Threat-hunting instruments depend on behavioral evaluation to study and perceive regular patterns of person and system conduct. They then make the most of methods resembling person and entity conduct analytics (UEBA), machine studying algorithms, and steady monitoring to establish anomalies, present context, and allow early menace detection. This characteristic additionally helps scale back false positives and enhances proactive identification and response to safety dangers.
Automated response
This characteristic prioritizes alerts based mostly on predefined standards, guaranteeing that important or recognized threats obtain speedy consideration. It consists of dynamic playbooks, integration with safety orchestration platforms, and actions resembling incident containment and isolation, person account remediation, and alert prioritization. With automated responses, organizations can scale back dwell time, make incident response extra environment friendly, and obtain compliance with safety insurance policies whereas guaranteeing that their community and techniques are protected towards safety dangers and threats.
How do I select the perfect cyber threat-hunting device for my enterprise?
Choosing the perfect cyber threat-hunting device on your particular person or enterprise wants borders on many elements, together with your private or enterprise goals, how the device matches into your present safety infrastructure and your price range. These seven instruments are nice threat-hunting instruments, relying in your private/enterprise wants.
For instance, for those who want a devoted menace looking service on high of the menace looking answer, one thing like ESET Enterprise Inspector is your greatest wager. On the opposite hand, if a single motion remediation that encompasses scanning, quarantine, and isolation together with an in-depth incident investigation is your purpose, then the Heimdal Threat Hunting and Action Center is your best choice. The identical applies to different instruments, as they every have a singular method to menace looking and remediation.
However, as with all device, its effectiveness will rely on how properly it’s built-in into a company’s current infrastructure and safety protocols. It’s all the time beneficial to guage these instruments within the context of your group’s particular wants and challenges.
Review methodology
For this evaluation, I thought-about necessary options of threat-hunting options, the varied approaches every device makes use of to detect threats, their remediation processes, integration capabilities with current techniques, and whether or not the distributors provided personalised help. I gathered info from the completely different distributors’ web sites and evaluation websites like Gartner to achieve extra perception on every device. I additionally thought-about the builders’ reputations and the place they stand within the trade.






